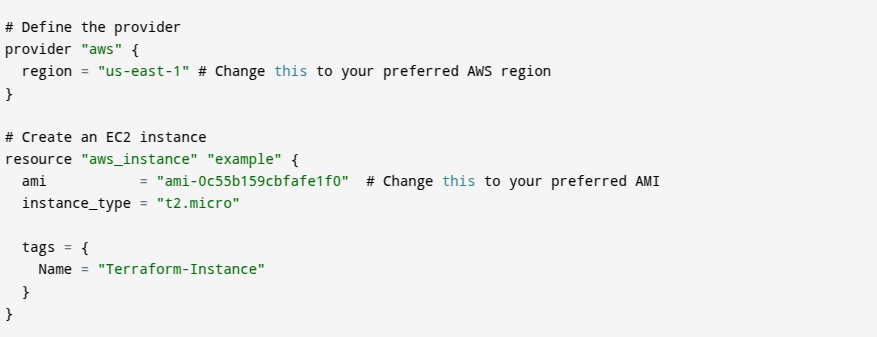
Imagine setting up cloud infrastructure in minutes without manual clicks or errors. That’s the power of Terraform, the industry-leading Infrastructure as Code (IaC) tool by HashiCorp. With Terraform, you define, provision, and manage cloud and on-premises resources effortlessly using simple, declarative configuration files.
Why waste time on repetitive tasks when you can automate everything? Whether you’re deploying AWS, Azure, or Google Cloud, Terraform helps you achieve consistency, scalability, and speed.
In this guide, you will go from zero to expert, learning:
-
- 1. What Terraform is and why you need it
-
- 2. How to write powerful Terraform configurations
-
- 3. Best practices to avoid costly mistakes
-
- 4. A step-by-step demo to deploy AWS resources
Get ready to transform the way you manage infrastructure with automation and efficiency.
What is Terraform?
- Terraform is an open-source tool that helps you manage infrastructure as code (IaC). With Terraform, you define your infrastructure using a simple language called HCL (HashiCorp Configuration Language). It works with multiple cloud providers like AWS, Azure, and Google Cloud, as well as on-premises systems. Instead of manually setting up servers, networks, and databases, you write a configuration file, and Terraform builds everything for you. This makes infrastructure setup faster, more consistent, and easier to track. You can also update and destroy resources using simple commands. Terraform is useful for developers, system administrators, and DevOps engineers who want to automate cloud infrastructure. Learning Terraform can help you manage large-scale systems efficiently and reduce human errors.
Key Features of Terraform
1. Declarative Syntax
- You describe what you want, and Terraform figures out how to create it. Instead of writing step-by-step commands, you define your infrastructure in a configuration file. Terraform automatically builds and updates resources based on your definition.
2. Multi-Cloud Support
- You can manage AWS, Azure, Google Cloud, and even on-premises systems using the same tool. This makes it easier to work with different cloud providers without learning multiple tools.
3. State Management
- Terraform keeps track of your infrastructure state in a state file. This helps detect changes, avoid configuration drift, and apply only necessary updates.
4. Modularity
- You can reuse configurations by creating modules. Instead of writing everything from scratch, you organize infrastructure code into reusable parts, making management simpler.
5. Infrastructure as Code (IaC)
- You write configuration files to define infrastructure instead of setting it up manually. This makes deployments faster, repeatable, and error-free.
6. Plan and Apply Workflow
- Terraform provides a plan before making changes. You can preview what will happen before applying updates, reducing mistakes.
7. Dependency Management
- Terraform automatically handles dependencies between resources. For example, it ensures a database is created before connecting a web server to it.
8. Version Control Integration
- You can store Terraform configuration files in Git or other version control systems, making collaboration and tracking changes easier.
9. Rollback and Recovery
- If something goes wrong, you can roll back to a previous version using the state file, ensuring system stability.
Why Use Terraform?
- Terraform is a powerful tool for automating infrastructure and making cloud management easier. Here are its key benefits:
1. Automation:
- With Terraform, you don’t need to manually set up servers, databases, or networks. Instead, you write configuration files, and Terraform builds everything for you. This saves time, reduces errors, and increases efficiency.
2. Consistency:
- Terraform ensures that your development, staging, and production environments are identical. This helps avoid issues where code works in one environment but fails in another.
3. Version Control:
- You can store Terraform configuration files in Git or other version control systems. This lets you track changes, collaborate with your team, and roll back to a previous version if something goes wrong.
4. Scalability:
- Whether you need one server or a thousand, Terraform makes scaling easy. You can quickly add or remove cloud resources without manual intervention.
5. Cost Efficiency:
- By defining exact resource requirements, Terraform prevents over-provisioning, helping you save on cloud costs. You only use and pay for what you need.
Using Terraform helps you manage large-scale infrastructure effortlessly while improving efficiency, reliability, and cost control. It is a must-have tool for DevOps engineers and cloud professionals.
How to Install Terraform
- You can install Terraform on Linux, macOS, or Windows using different methods. Here’s a step-by-step guide for you:
1. Installing Terraform on Linux:
- a. You need to use the “wget” command to download the Terraform binary from HashiCor’s official Website:
- https://developer.hashicorp.com/terraform/downloads (Copy the link of the latest version)
- b. After downloading this Terraform binary file, which is in “.zip” format, now you need to extract it:

- c. After unzipping this file, you should make Terraform available from anywhere in your terminal, so you move this Terraform binary file to a system directory:

- This allows you to run Terraform commands globally without specifying the file path.
- d. To verify the installation, you need to check if Terraform is installed correctly by running:

- e. You should see the installed Terraform version displayed. (Linux)

2. Installing Terraform on Windows:
- a. First, you need to download the latest Terraform Version for the “Windows” from the official website:
- b. After downloading the file, extract the “ZIP” file to [C:\terraform]
- c. Then you need to add terraform to the System Path for available globally at your local machine:
- 1. First, Open Control Panel > System > Advanced system settings.
- 2. Then, click Environment Variables > Path > Edit.
- 3. Click New, then add C:\terraform.Click OK and restart PowerShell.
- d. Now you need to verify whether Terraform is successfully installed or not:

Terraform Basics: HCL Syntax
- Terraform uses HashiCorp Configuration Language (HCL) to define and manage infrastructure as code (IaC). HCL is a declarative language, meaning you describe the desired state of your infrastructure, and Terraform ensures it is created or updated accordingly.
- Terraform HCL syntax allows you to define infrastructure in a readable and structured manner.
-
- 1. Providers define the cloud service. (aws, azure, google)
-
- 2. Resources specify what infrastructure to create. (aws_instance, aws_vpc )
-
- 3. Variables make configurations flexible.
-
- 4. Outputs return values after deployment.
a. Basic Terraform Configuration Example
- Here’s a simple Terraform configuration file (
main.tf):
b. Breakdown of Key Components
1. Provider
-
- 1. The provider block specifies the cloud service provider.
-
- 2. Terraform supports multiple providers like AWS, Azure, Google Cloud, etc.
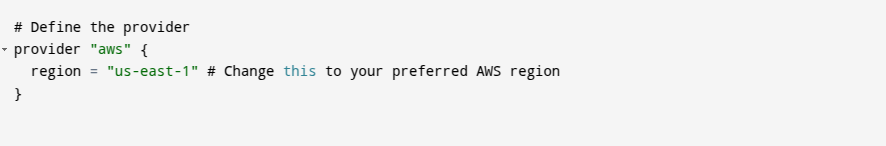
- In this example,
"aws"is the provider, and the region “us-east-1” is specified. This tells Terraform to deploy resources in the AWSus-east-1region.
2. Resource
- The resource block defines the infrastructure that Terraform should create.
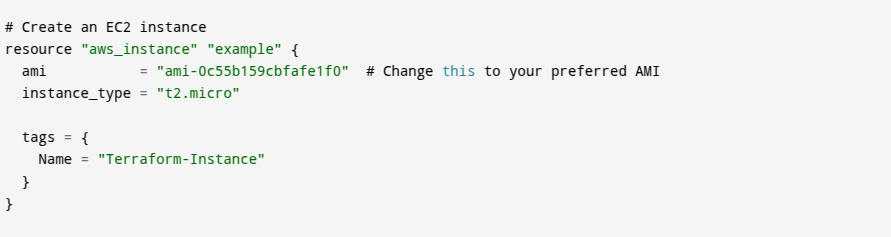
"aws_instance"is the resource type (which means an EC2 instance in AWS), and"web"is the resource name (used to reference this instance in Terraform).
- ami: The Amazon Machine Image (AMI) ID (
ami-0c55b159cbfafe1f0), instance_type: The EC2 instance type (t2.micro), tags: Metadata to identify the instance (Name = "WebServer").
3. Variables
- Variables allow dynamic inputs instead of hard-coded values.

- Then, instead of hardcoding
"t2.micro", you use:

- This makes the configuration reusable and flexible.
4. Outputs
- Outputs provide useful information after deployment.

- After applying Terraform, the public IP of the created EC2 instance is returned.
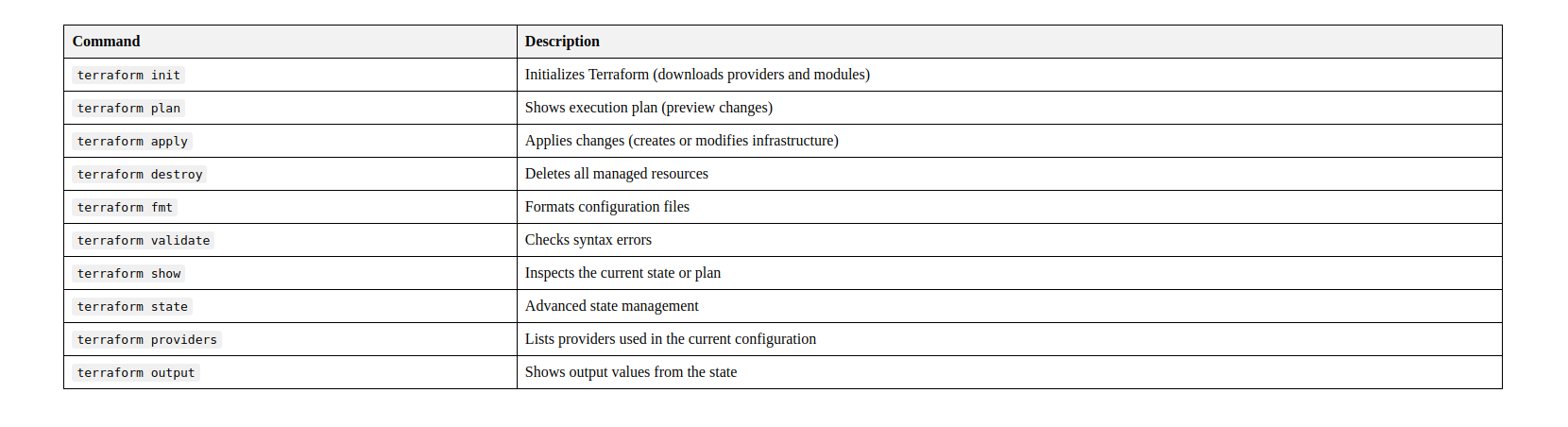
Core Terraform Commands – Explained Simply
- Terraform is a tool that helps you create and manage cloud resources using code. To use Terraform effectively, you need to understand its core commands. These commands allow you to initialize, preview, apply, format, validate, and destroy your infrastructure.
a. terraform init – Start Terraform
- This “terraform init” command initializes Terraform in your project folder. It downloads necessary providers (like AWS, Azure, or Google Cloud) and sets up Terraform’s working directory. If you’re using AWS, Terraform will download the AWS provider plugin the first time you run it. Without running init, Terraform won’t know which cloud services to use.
b. terraform plan – Preview Changes
- This “terraform plan” command shows what Terraform will do before making changes. It helps you review the impact of your changes before actually applying them. It prevents mistakes by showing if Terraform will create, update, or delete anything.
c. terraform apply – Create Infrastructure
- This “terraform apply” command creates or updates your cloud infrastructure based on your configuration file. Terraform will first ask for confirmation before making changes. Terraform will display the execution plan again and ask: Do you want to perform these actions? (yes/no). It actually creates the resources in the cloud.
d. terraform destroy – Remove Everything
- This “terraform destroy” command deletes all the cloud resources that Terraform has created. It’s useful when you no longer need the infrastructure or want to start fresh. Terraform will ask for confirmation before deleting. It helps avoid unwanted costs by removing unused cloud resources.
e. terraform fmt – Format Code
- This “terraform fmt” command automatically formats your Terraform configuration files, making them easier to read. It keeps your code clean, consistent, and readable.
f. terraform validate – Check for Errors
- This “terraform validate” command checks your Terraform files for syntax errors before running them. It helps catch mistakes early, preventing failures when running applications.
g. terraform show – View the Current State
- This “terraform show” command displays information about the infrastructure that Terraform has created. This will print details about all resources Terraform is managing, such as the resource type (e.g., aws_instance), the resource name (e.g., web), and any attributes (like public IP, instance type, etc.). It helps you understand the current state of your infrastructure.
h. terraform state – Manage the State File
- Terraform keeps track of all resources in a file called the state file (terraform.tfstate). The “terraform state” command helps you view, modify, and remove entries in the state file. It helps you inspect and modify Terraform’s tracking of resources & it can be useful if Terraform gets out of sync with the actual cloud infrastructure.
i. terraform import – Bring Existing Resources into Terraform
- Normally, Terraform creates resources from scratch. But what if you already have resources in AWS, Azure, or Google Cloud and want Terraform to manage them? You use “terraform import” to bring those resources under Terraform’s control. It helps migrate existing infrastructure into Terraform & prevents Terraform from creating duplicate resources.
j. terraform providers – Show Providers in Use
- This “terraform providers” command lists all cloud providers that Terraform is using in your project. It helps you check which providers are being used & it is also useful when debugging provider version issues.
Terraform State Management Overview
- Terraform keeps track of your infrastructure using a state file (
terraform.tfstate). This file records the current configuration and resource details.
a. Best Practices for Managing Terraform State
- The image lists three key best practices:
1. Remote State
-
- 1. Store the state file in S3 (Amazon Simple Storage Service) + DynamoDB or Terraform Cloud instead of your local machine.
-
- 2. This ensures that multiple team members can access the same infrastructure state.
2. State Locking
-
- 1. Prevents multiple users from making changes at the same time.
-
- 2. Using DynamoDB helps avoid conflicts when multiple people run
terraform applysimultaneously.
- 2. Using DynamoDB helps avoid conflicts when multiple people run
3. Backups
-
- 1. Always create versioned backups of state files to prevent data loss.
-
- 2. If a mistake happens, you can restore a previous version.
b. Example: Storing Terraform State in AWS S3
The image provides an example of how to configure remote state storage in AWS S3.
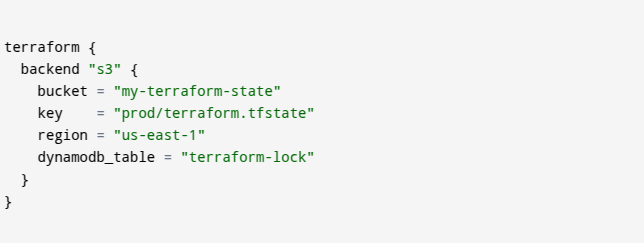
Explanation of Each Line
-
- 1. terraform {} → Defines backend storage for Terraform state.
-
- 2. backend “s3” {} → Specifies that Terraform will store the state file in an S3 bucket.
-
- 3. bucket = “my-terraform-state” → The S3 bucket name where the state file is stored.
-
- 4. key = “prod/terraform.tfstate” → The file path inside the S3 bucket.
-
- 5. region = “us-east-1” → The AWS region where the S3 bucket is located.
-
- 6. dynamodb_table = “terraform-lock” → Enables state locking using DynamoDB to prevent conflicts.
c. Why Is This Important?
1. Collaboration:
- Helps teams work together on Terraform infrastructure.
2. Prevents Corruption:
- Protects the state file from accidental overwrites.
3. Disaster Recovery:
- Ensures that the Terraform state can be recovered if something goes wrong.
- This image explains Terraform Modules for Reusability, specifically how modules help reuse configurations and simplify infrastructure management.
Terraform Modules for Reusability
a. What Are Terraform Modules?
- Terraform modules are reusable sets of Terraform configurations. Instead of writing the same code multiple times, you can create a module and use it in different projects.
b. Benefits of Using Modules
1. Reusability
- Define infrastructure once and reuse it across multiple environments.
2. Maintainability
- Easier to update and manage configurations.
3. Consistency
- Ensures that all infrastructure follows the same best practices.
c. Example: Using a Terraform Module for VPC
- The image provides an example of how to use a Terraform module to create a Virtual Private Cloud (VPC) in AWS.
1. Terraform Code
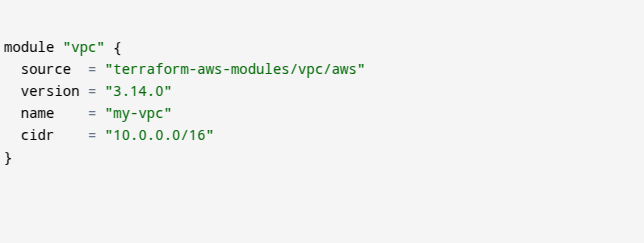
2. Explanation of Each Line
-
- 1. module “vpc” {} → Defines a module named vpc.
-
- 2. source = “terraform-aws-modules/vpc/aws” → Specifies the source of the module.
-
- 3. This module is pre-built and hosted in the Terraform Public Module Registry.
-
- 4. version = “3.14.0” → Specifies the module version to ensure stability.
-
- 5. name = “my-vpc” → Sets the VPC name.
-
- 6. cidr = “10.0.0.0/16” → Defines the IP range for the VPC.
d. What Is the Terraform Module Registry?
- The Terraform Public Module Registry is an online repository where you can find pre-built Terraform modules for different cloud providers like AWS, Azure, and Google Cloud. Link to the Public Module Registry: Terraform Registry
e. Why Use Terraform Modules?
-
- Saves time by using existing, well-tested modules.
-
- Improve security by following best practices.
-
- Simplifies large projects by breaking them into smaller components.
Step-by-Step Demo: Deploying AWS Infrastructure
Step 1: Configure AWS Credentials
- To let Terraform access your AWS account, you must provide security credentials.

- What This Does:
-
- 1. These environment variables give Terraform permission to use your AWS resources.
-
- 2. Replace
"YOUR_ACCESS_KEY"and"YOUR_SECRET_KEY"with the actual credentials from your AWS IAM user (with EC2 access permissions).
- 2. Replace
-
- 3. Alternatively, you can configure this once using: aws configure
Step 2: Create main.tf
- This is the Terraform configuration file. Save it “
main.tf” in your working directory.
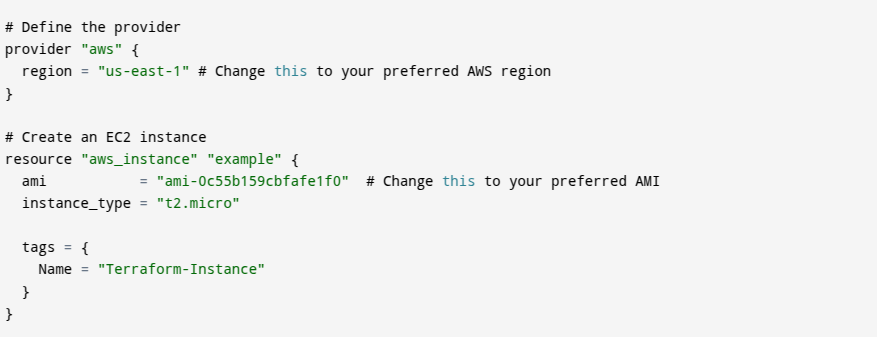
What This Does:
-
1. provider "aws": Specifies that we are using the AWS cloud provider.
-
2. region = "us-east-1": The AWS region where the instance will be created (e.g., N. Virginia).
-
3. resource "aws_instance": Tells Terraform to create an EC2 instance.
-
4. ami: The ID of the base operating system image (in this case, Amazon Linux).
-
5. instance_type: Defines the compute power (e.g.,t2.microis suitable for small workloads and is free-tier eligible).
-
6. tags: Helps label and organize your AWS resources.
Step 3: Initialize & Apply
Run These Commands in Your Terminal:

What These Do:
-
1. terraform init: This initializes Terraform in the current directory. It downloads necessary plugins (like AWS).
-
2. terraform plan: Shows what changes Terraform will make (a dry run).
-
3. terraform apply -auto-approve: Applies the configuration without asking for confirmation, i.e., creates the EC2 instance on AWS.
Step 4: Verify in the AWS Console
-
- 1. Go to AWS EC2 Dashboard.
-
- 2. Check the running instances section.
-
- 3. You should see a new instance named “WebServer” in the us-east-1 region.
Step 5: Clean Up

What This Does:
-
- 1. This command deletes the EC2 instance (and any other resources created by Terraform).
-
- 2. It’s important to destroy unused resources to avoid unexpected charges.
Best Practices for Terraform
a. Use Remote State
- Don’t store Terraform state files (
terraform.tfstate) locally. Instead, AWS S3 can be used with DynamoDB or Terraform Cloud. This prevents data loss and allows team collaboration.
b. Modularize Configs
- Instead of writing the same code again, create Terraform modules. Modules help you reuse code, making infrastructure easier to manage and update.
c. Version Control
- Store
.tffiles in Git (GitHub, GitLab, or Bitbucket). This helps you track changes, roll back updates, and collaborate with others.
d. Use Variables
- Avoid hardcoding values like region names or instance types. Instead, use Terraform variables (
variables.tf) for flexibility.
e.Plan Before Apply
- Run
terraform planbeforeterraform applyto preview changes and avoid mistakes.
f. Secure Secrets
- Never store sensitive data in
.tffiles. Use AWS Secrets Manager or Vault to store passwords and API keys safely.
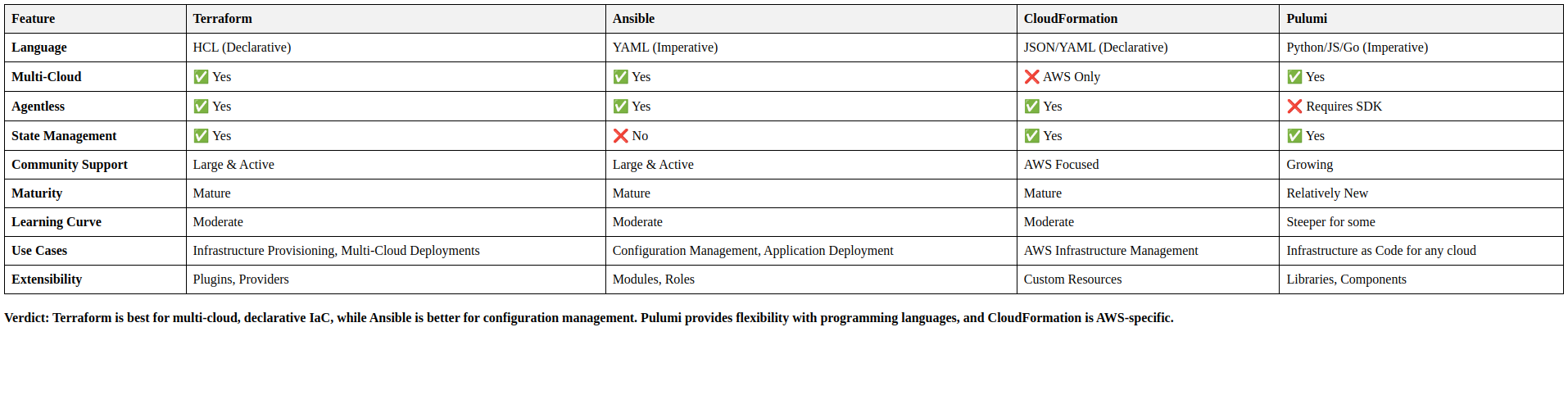
Terraform vs. Other IaC Tools
Conclusion
- Terraform simplifies infrastructure automation by enabling you to define, provision, and manage resources with code. You have learned how to write HCL-based configurations, execute core commands (
init,plan,apply,destroy), manage state efficiently, and reuse configurations through modules. These concepts form the foundation of Infrastructure as Code (IaC), ensuring consistency, scalability, and automation.
- The next step is to explore Terraform Cloud for team collaboration, dive into advanced modules for Kubernetes and databases, and integrate Terraform into CI/CD pipelines for continuous automation. By following best practices—such as using remote state, securing secrets, and modularizing code—you can create a more reliable and scalable infrastructure.
- With Terraform, infrastructure deployment is no longer manual or complex. It becomes a streamlined, automated process that reduces errors and enhances efficiency. Start leveraging Terraform today to build and manage cloud environments seamlessly while ensuring long-term scalability and operational excellence.